This article assumes you have already installed the PuTTY suite of applications.
- Unprotected Private Key File Ssh
- Private Key File Ssh
- Putty Private Key File Ssh
- Invalid Private Key File Ssh.net C#
- Windows Ssh Private Key File
The key files are stored in the /.ssh directory unless specified otherwise with the -ssh-dest-key-path option. If an ssh key pair already exists and the -generate-ssh-keys option is used, a new key pair will not be generated but instead the existing key pair will be used. In the following command, replace VMname and RGname with your own. $ ssh-keygen On execution, we are prompted to specify a file in which to save the private key, the default being /home/user/.ssh/idrsa; here idrsa is the name of our Private Key file. You can always specify a different path and name for the Private Key file.
Public/private key authentication, as the name suggests, uses two special cryptographic text files (called keys) to authenticate your login. The private key remains on your computer and should be kept safe from unauthorised access. The public key can be freely installed on remote systems. It doesn't matter if your public key gets stolen or lost. Because only you have the private key you can always regenerate the public key again from it. The key files are just plain text - nothing magical. You can open them in notepad if you are curious!
- Generate your public/private key pair
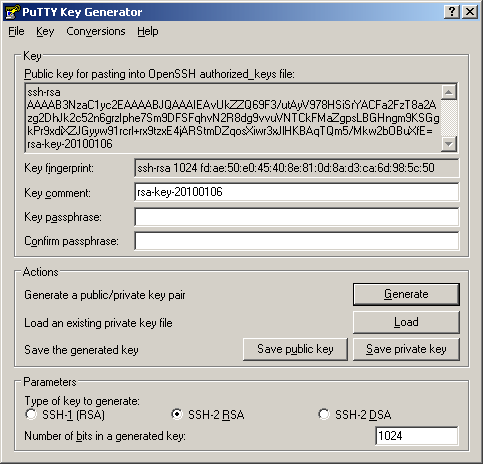
Start PuTTYgen, and choose a type of key to generate and keysize. If you are unsure what to choose, just copy the settings shown below.Click the Generate button.
PuTTYgen will then ask you to wiggle your mouse around for a while to help it generate the key.When you've shuffled your key around the area enough, the green bar will reach the right side and PuTTYgen will create your keypair and you will see something like this:Just fill in the Key comment field (your name is a good idea), and enter a STRONG passphrase including upper and lowercase letters, numbers, and symbols. Keep this passphrase somewhere secure so you can get to it later (you'll need it anytime you want to use your private key from a new computer).
If your private key ever gets stolen, this password is your last line of defence. A private key with a weak or no passphrase is a gift to hackers! Generally speaking, a good 16 character passphrase will keep the world's most powerful computers at bay until the sun burns out!
Click the Save private key button and save your private key with the .ppk extension (you'll need this file later in this guide).
Your public key doesn't need saving because it can always be generated instantly from the private key - but don't close PuTTYgen yet because we're going to do some cPanel magic. - Setting up your cPanel account with your public key
Log into your cPanel account, and click on the SSH Access icon in the Security group of icons.Click the Manage SSH Keys button.Click the Import Key button to get the Import SSH Key screen.Now, switch back to PuTTYgen, and select ALL of the text in the box at the top entitled Public key for pasting into OpenSSH authorized_keys file: and copy it.Switch back to cPanel again, and paste in your public key into the public key text box. Give your public key a name, as shown (this becomes the filename your public key is saved as) and click the Import button. If you don't give your key a name, it will default to being called id_dsa.The next step is to authorise your public key.Back on the Manage SSH Keys cPanel screen, click Manage for your key (as shown)
Then, on the Manage Authorization screen just click the Authorize button and you should receive a confirmation that the key has been authorised. That's it, you're now ready to use your private key! - Configuring Pageant to decode your private key for PuTTY and Filezilla
OK, remember back in Step 1, we saved your private key with a .ppk extension?
Open the Pageant application (part of the PuTTY tools that you installed already).
Did nothing happen? That's OK - Pageant only runs as a small taskbar icon (It looks like a little PC with a hat on).Now, right-click the little Pageant icon, and a context menu will pop up. Select Add Key from the popup menu.This will open a file selection window. Simply browse to wherever you saved your .ppk (private key) file in Step 1 and click Open.
You did remember to store that strong passphrase from Step 1 somewhere, didn't you? Enter it in the text box and click OK.That's it. Pageant now has your private key open and ready for use by other applications. You can check your keys by right-clicking Pageant and selecting View Keys.
Or, and this is the neat part, you can right-click Pageant, and hover your mouse over the Saved Sessions menu item to reveal any Saved Sessions from PuTTy. You only need to click on your saved session to connect automatically to your SSH session without having to start PuTTY yourself.
Enhancing SFTP Access using Filezilla with public/private keys
Assuming you have already Setup Filezilla to connect using SFTP with your account password, then there is very little to do
Just open Filezilla's Site Manager from the File menu, locate your connection profile under My Sites, and remove the password.
As long as Pageant is doing its thing in the taskbar, then Filezilla will automatically try to connect using your private key.
How did we do?
Related Articles
Private keys allow the users to login to SSH without a password. This is considered a safe practice in some cases while also discards the need to remember multiple passwords.
In this tutorial, we would learn how to generate our own SSH Key Pair on our local machine and then configure our Server to use the same for authentication when trying to connect over SSH.
Steps to Login to SSH Without A Password
Let’s go over the process step-by-step to login to SSH without a password. If you’re new, you can start by reading more about how to connect to a remote host using SSH. If you’re ready, let’s get started.
Step 1: Generate SSH Key Pair
On our local machine, we can generate a SSH Key Pair with the following command :
On execution, we are prompted to specify a file in which to save the private key, the default being /home/user/.ssh/id_rsa ; here id_rsa is the name of our Private Key file. You can always specify a different path and name for the Private Key file. For our demonstration, we shall use the default configuration.
Unprotected Private Key File Ssh
Step 2: Provide A Passphrase (Optional)
Next, we are presented with a prompt that asks us for a passphrase that can be used to protect the SSH Private Key from unauthorized access.
However, this field is optional and if left empty, it stores the Private Key file without any protection. In our example, we would leave this field empty. After this, we would have successfully generated our Key Pair. We are also presented with a ‘fingerprint’ and ‘visual fingerprint’ of our key which we need not save.
Step 3: Configure the Server To Use Our Private Key
At this point, we should have the following two files under /home/user/.ssh :
- id_rsa : Our SSH Private Key
- id_rsa.pub : Our SSH Public Key
Take note of the permissions of the private key ( id_rsa ). SSH Private Key files should ALWAYS HAVE 600 PERMISSIONS! If not, change its permission to the said value using the chmod command:
Next, we need to configure our Server to use our private key for login. Now this can be done manually by logging into the Server and configuring stuff manually but there’s a tool ssh-copy-id which does all the hard work for us !
Hence, to configure our Server to use our private key, simply run :
Here,
Private Key File Ssh
- USER is the username we want to login as onto the server
- IP is the IP address of our Server

And with that, we can now simply SSH into our Server with :
Putty Private Key File Ssh
If you had previously specified a passphrase, you will get a prompt asking for the same :
Note that if you are not using the default path and file names then you need to specify the private key file using the -i flag as follows :
Invalid Private Key File Ssh.net C#
Thus we successfully SSH’d into our machine using our PRIVATE KEY !
Windows Ssh Private Key File
Conclusion
And with that, we were able to login to SSH without a password on our Linux machine. It’s an easy and more secure way of logging in as it locks you to log in from specific IP addresses. If you’re interested in learning more on Linux topics, continue to follow LinuxForDevices.
